Cyble, an information cybersecurity company, has discovered data of half a million Zoom video conferencing service accounts on the darknet. The databases include email addresses, passwords, the service meeting URLs, and host keys.
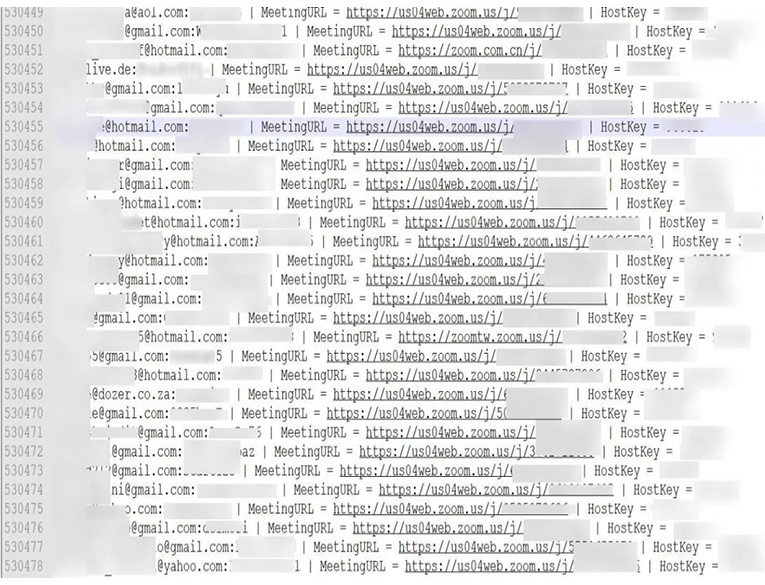
Zoom user accounts began appearing on various hacker forums on April 1. Each account was sold for less than a cent, and some were even available for free. This way, attackers tried to earn a reputation in the hacker community.
The discovered data turned out to be the result of an attack of the credential stuffing type — user logins and passwords were stolen from one service, and hackers tried to gain access to other services using the received credentials.
In open databases, Cyble specialists found accounts that have connections with large companies such as Chase and Citibank. Moreover, the found compromised account information was related to American educational institutions, such as the University of Florida or Dartmouth College.
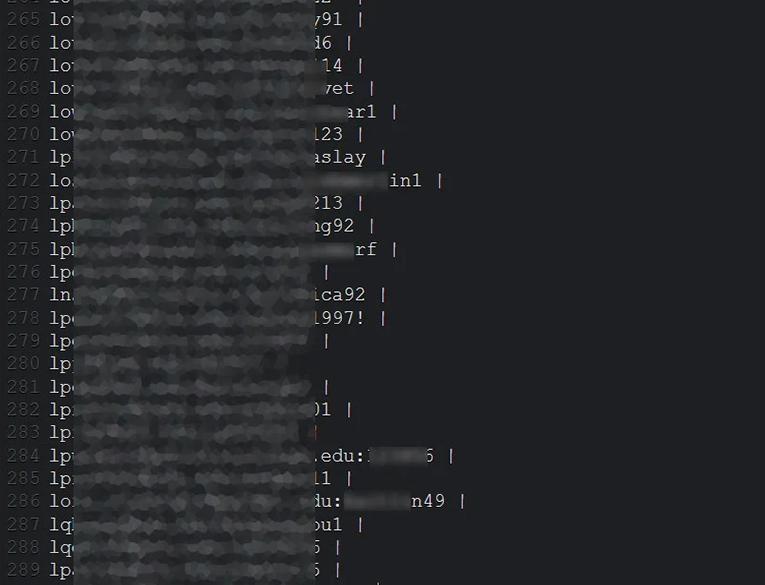
Cybersecurity company decided to redeem about 530 thousand accounts in bulk for 0.002 cents each. It allowed specialists to warn customers about the danger.
The media has repeatedly reported the leak of several thousand personal video calls made through the Zoom video conferencing service. Leaked videos appeared in the public domain on YouTube and Vimeo. All this is because Zoom assigns open identifiers to video conferences and does not encrypt the connection.
By the beginning of April, the number of daily Zoom users exceeded 200 million. The service promised to fix detected problems with the security and privacy of conferences within 90 days.